An All In One Security Appliance Is Best Suited For Which Type Of Implementation
An all in one security appliance is best suited for which type of implementation. Your Cisco router has three. I am looking for a solution that is a single brand HP Cisco Dell and so on I have 20 locations including a corporate office each area has between 4 and 20 computers connected to an HP 1910. Close all ports open only ports required.
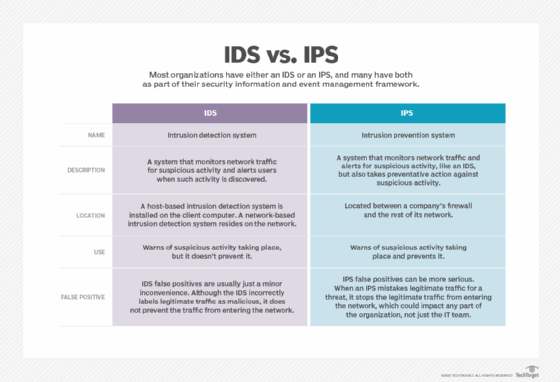
Most commonly these functions are firewall IDSIPS and antivirus although all-in-one appliances can include VPN capabilities anti-spam malicious web traffic filtering antispyware content filtering traffic. Need to be onboard for the implementation. Each site has two Wireless access points one inside and one outside.
And a company that handles large amounts of data should use dedicated devices to maintain optimal performance. There are several factors to consider before buying an all-in-one security appliance. Which firewall implementation creates a buffer.
A company with a dedicated network closet would have the spaced necessary for multiple networking devices. A company with a dedicated network closet would have the space necessary for multiple network devices. An All-in-one security appliance is best.
Layer 2- V Layer 3- R Counts-R Does-V Different-R Same-V. A company that handles large amounts of data should use dedicated devices to maintain optimal performance. Which of the following are true about routed firewalls.
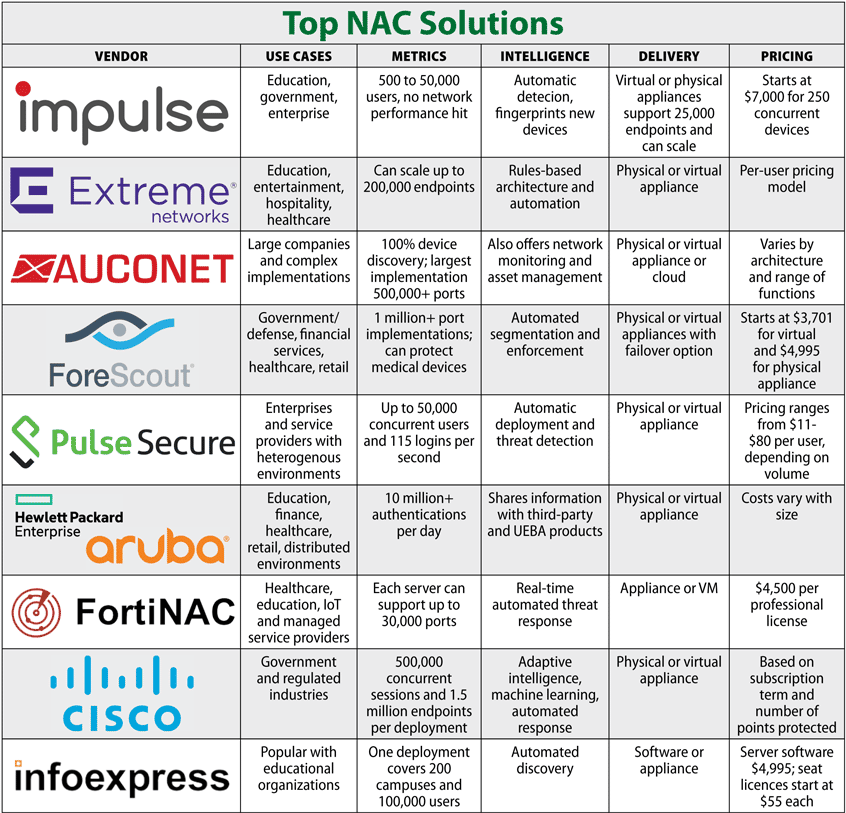
All in one security appliances are best suited for small offices with limited space or remote offices without a technician to manage the individual security components. May not provide the best features in an overarching solution. A Look at All-in-One Security Appliances.
All-in-One Firewall IPS and VPN Adaptive Security Appliance is a practitioners guide to planning deploying and troubleshooting a comprehensive security plan with Cisco ASA. Those point solutions may give greater security protection than a one-size-fits-all UTM appliance but they can come with management implementation and integration challenges too.
I am looking for a solution that is a single brand HP Cisco Dell and so on I have 20 locations including a corporate office each area has between 4 and 20 computers connected to an HP 1910.
Need to be onboard for the implementation. Explanation All-in one security appliances are best suited for small offices with limited space or a remote office without a technician to manage the individual security components. The book provides valuable insight and deployment examples and demonstrates how adaptive identification and mitigation services on Cisco ASA provide a. Layer 2- V Layer 3- R Counts-R Does-V Different-R Same-V. Explanation All-in one security appliances are best suited for small offices with limited space or a remote office without a technician to manage the individual security components. VCenter Server Standard High-end management enabling the optimization and control of all VMs in a vSphere environment. The implementation of these editions is impossible without a search function a vSphere client a web access portal a management server a database server vCenter APIs and a NET extension. The traditional implementation of WAFs is still a great one and that is by deploying an appliance on an organizations network usually between its Web application and the users accessing it. Those point solutions may give greater security protection than a one-size-fits-all UTM appliance but they can come with management implementation and integration challenges too.
VCenter Server Standard High-end management enabling the optimization and control of all VMs in a vSphere environment. A remote office with no on-site technician. Explanation All-in one security appliances are best suited for small offices with limited space or a remote office without a technician to manage the individual security components. An all-in-one security appliance is best suited for which type of implementation. Which firewall implementation creates a buffer. The book provides valuable insight and deployment examples and demonstrates how adaptive identification and mitigation services on Cisco ASA provide a. Layer 2- V Layer 3- R Counts-R Does-V Different-R Same-V.



















Post a Comment for "An All In One Security Appliance Is Best Suited For Which Type Of Implementation"